For more information on your charming neighborhood CSW Solutions, visit us at our home or subscribe to our newsletter! We also do that social networking thing at: Twitter, Facebook, Linkedin, and Instagram! Check out our #funfactfridays
Security-First Development: Why Modern Software Has to Be Secure from the Start
Software is no longer just a tool that powers business operations, it is the business. Every workflow, every customer interaction, every automated process, and every strategic decision depends on it. However, this reliance brings about a challenging truth: the potential for attacks has expanded beyond what we've seen before, and threats are constantly evolving at a pace that traditional development cycles struggle to keep up with.
Many security breaches nowadays do not necessarily stem from a sophisticated or rare zero-day exploit. Instead, they frequently result from easily preventable vulnerabilities: a misconfigured API, an overlooked known vulnerability in a dependency, an exposed privileged role, a long-forgotten secret hard-coded in a repository with no updates.
Organizations have responded to this urgency with a mindset shift: Security-First Development — building secure, resilient systems from inception rather than scrambling to bolt protection on after the fact. It’s a philosophy, but also a practical framework supported by modern practices like DevSecOps, Software Bills of Materials (SBOMs), Zero Trust architectures, and secure-by-design engineering.
This post dives into what that shift looks like, why it matters, and how organizations can adopt it without slowing innovation.
Why "Security-First" Is No Longer Optional
There was a time when security entered the picture only after the code was deployed often months, sometimes years after its first commit. This approach to security in the software development process was not only inefficient but also risky. Security teams would run scans, fix bugs, and developers would scramble to patch issues long after the project was live. This reactive approach meant that security fixes were often rushed and not thoroughly tested, leading to potential vulnerabilities being missed.
But that world is gone.
These days, attackers automate vulnerability discovery at scale. They monitor public repositories for exposed credentials. They track every new CVE published, often exploiting it automatically within hours of disclosure. Meanwhile, businesses depend on a tangled ecosystem of SaaS tools, microservices, cloud APIs, and open-source libraries.
The result?
-
73% of organizations experienced at least one ransomware attack in the last year.
-
Open-source components make up more than 80% of modern application code.
-
The average time-to-exploit for new vulnerabilities is often within days.
Security is a crucial aspect of any organization's operations, and it should not be treated as an afterthought. Instead, security needs to be integrated into every decision made - whether it's related to architecture, operations, or culture. This is where the concept of Security-First Development comes into play. By following the pillars of Security-First Development - architectural, operational, and cultural - organizations can create a secure environment that protects their data, systems, and reputation.`
DevSecOps: Embedding Security into the Entire Pipeline
If DevOps was about accelerating delivery, DevSecOps is about accelerating delivery safely.
It represents a transformative change: instead of security being a separate gatekeeper function, it becomes a shared responsibility across development, operations, and cybersecurity teams. It replaces long feedback loops with continuous, automated verification. By incorporating security practices early on in the development lifecycle, DevSecOps aims to identify and address potential vulnerabilities before they become major issues. This shift helps to create a more secure and resilient software development environment.
The Core Principles of DevSecOps
DevSecOps rests on a few fundamental ideas:
- Security must be continuous
This means that security processes and measures should be seamlessly integrated throughout the entire software development lifecycle, from planning and coding to testing and deployment. Every commit, build, test, and deployment should automatically run through the appropriate security checks — from SAST and DAST tools to dependency scanning to container image validation. - Security should "shift left"
Traditionally, security entered the lifecycle just before release. Shifting left means bringing it earlier — at design, coding, and build stages — where fixing issues is far easier and cheaper. This shift left approach helps to create a more secure and robust final product, ultimately reducing the risk of security breaches and incidents down the line. It also promotes a culture of security awareness and responsibility among developers, leading to better overall security posture for the organization. - Everyone owns security
Developers write secure code. Operations ensures secure infrastructure. Security teams build guardrails, not roadblocks. The entire organization shares responsibility. By empowering everyone to take ownership of security, issues can be identified and addressed more quickly and effectively. This collaborative approach to security helps to ensure that security is integrated into every stage of the development process, leading to more secure and resilient software products. - Automate everything
Scanning code, checking infrastructure, and even validating configurations, if a process can be automated, it should be. By automating processes such as testing, deployment, and security checks, teams can save time and reduce the potential for human error. It also allows for more frequent and consistent testing, which can help to identify and address security vulnerabilities more effectively. Teams can streamline workflow, improve efficiency, and ultimately enhance the security of their software applications.
What DevSecOps Looks Like in Practice
Integrated security scanning in CI/CD
Modern pipelines use tools like GitHub Advanced Security, GitLab SAST, or Azure DevOps security tasks to automatically:
- Identify vulnerable dependencies
- Scan source code for common security issues
- Analyze container images
- Validate configurations against known baselines
- Developers get feedback instantly, not weeks later.
Infrastructure as Code (IaC) validation
IaC templates (Terraform, Bicep, ARM) are scanned for misconfigurations, closing off common cloud vulnerabilities like open S3 buckets or permissive firewall rules. This proactive approach to security not only helps prevent costly breaches and downtime but also ensures that cloud resources are used effectively. By integrating IaC validation into the development and deployment process, organizations can build a more secure and reliable cloud infrastructure.
Secrets management
Hardcoded secrets are eliminated in favor of vaults (Azure Key Vault, HashiCorp Vault, AWS Secrets Manager), and pipelines enforce checks to prevent accidental exposure. By centralizing and securely storing secrets in vaults, organizations can ensure that sensitive information is protected and only accessible to authorized users or systems.
Threat modeling
By proactively assessing high-risk areas before coding even begins, teams can identify potential vulnerabilities and weaknesses that need to be addressed. Techniques like STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) or attack-path mapping can help teams pinpoint where security controls need to be strongest.
Automated compliance
With DevSecOps, compliance is built directly into the pipeline — mapping each requirement (SOC 2, HIPAA, PCI, etc.) to a corresponding control and verification step. Organizations can streamline the compliance process and reduce the risk of non-compliance. This automated approach not only saves time and resources but also helps to maintain a high level of security and data protection.
SBOMs: Knowing What Your Software Is Made Of
If DevSecOps is the cultural backbone of Security-First Development, SBOMs are the inventory system. They answer a crucial question:
What exactly is in your software?
With supply chain attacks on the rise like SolarWinds, Log4j, dependency hijacking, and malicious NPM packages, organizations must understand their dependencies at a granular level.
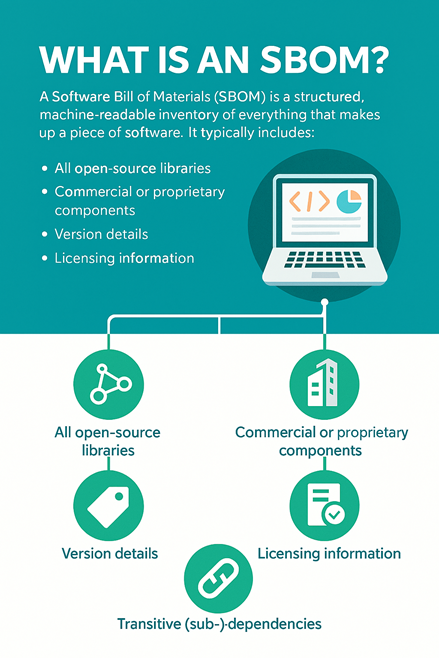
What Is an SBOM?
An easy way to think about it: an SBOM is like a nutritional label for software. It shows you exactly what’s inside so you can quickly identify where a vulnerability exists and understand how it affects your environment.
Why SBOMs Are Becoming Mandatory
Governments and major enterprises are increasingly requiring SBOMs. U.S. Executive Order 14028 requires SBOMs for software sold to federal agencies. Major tech companies like Microsoft and Google are deeply engaged with SBOM generation and transparency, and some government contractors (e.g., DoD suppliers) are being mandated to provide SBOMs. While cyber insurers are beginning to discuss SBOMs as part of risk management, publicly available evidence of SBOMs being a formal requirement in underwriting remains limited — though the trend is growing.
The Benefits of SBOMs in Security-First Development
1. Faster vulnerability response
When a new CVE emerges, organizations can automatically scan their SBOMs and determine:
- Are we using this library?
- Which version?
- Where is it deployed?
- What systems depend on it?
This reduces response time from days to minutes.
2. Improved supply chain governance
SBOMs help teams understand licensing risks, third-party dependencies, and the security posture of the components they rely on.
3. Reduced shadow dependencies
Many developers don’t realize their direct dependencies pull in dozens or hundreds of transitive dependencies. SBOMs expose this hidden attack surface.
4. Better vendor accountability
Organizations can mandate secure components, track patch levels, and standardize expectations for third-party software providers.
By having a clear understanding of what is in your software, developers and security teams can better assess potential vulnerabilities and make informed decisions about security measures. SBOMs also play a crucial role in compliance with regulations and standards, as they provide transparency and accountability in the software supply chain.y having a comprehensive SBOM, you are better equipped to manage and secure your software effectively, making it an indispensable tool.
Zero Trust Architecture: Never Trust, Always Verify
Security-First Development isn’t just about secure code — it’s also about secure systems. In the past, the traditional model of security relied on the concept of a castle-and-moat, where users inside the network were trusted, and those outside were not. However, with the rise of identity-based attacks, this model is no longer effective.
Zero Trust is a security concept that emphasizes the importance of never trusting, always verifying. No user, device, workload, or service is inherently trusted — even if it’s already “inside” the network.
The Core Philosophies of Zero Trust
Assume breach
Operate as if an attacker is already in the environment and design controls that minimize the blast radius.
Identity is the new perimeter
Authentication and authorization happen continuously, not just at login.
Least privilege everywhere
Users, workloads, APIs, service accounts — all receive only the permissions absolutely necessary.
Continuous verification
Trust is reevaluated constantly based on context:
- Device health
- User location
- Access behavior
- Anomalies
- Sensitivity of requested resources
Zero Trust in the Software Development Lifecycle
Zero Trust isn’t only about user access — it’s also about how applications behave.
Micro-segmentation of services
Applications in a Zero Trust environment must abide by strict policies dictating which services can talk to each other, what protocols and ports are allowed, and where traffic can originate. This prevents attackers from traversing laterally in microservices or cloud environments.
Strong identity for workloads
Every API, container, or function should have its own identity (managed through certificates, managed identities, or workload identities). No more shared service principals.
Continuous monitoring
Logs, telemetry, and behavioral analytics identify unusual access patterns quickly — enabling fast containment of threats.
Secure API communication
All internal and external API calls use mutual TLS, strong authentication tokens, and strict authorization requirements. Zero Trust ensures software is secure in operation, not just in design.
Secure-by-Design Coding: Building Security into Every Line of Code
Security-First Development ultimately depends on the habits and decisions of developers. Tools and processes help — but the foundation is a culture of secure-by-design engineering.
Secure-by-design coding means that security isn’t an add-on or an afterthought; it’s built into the DNA of every component from the moment the first file is created.
The Principles of Secure-by-Design Engineering
1. Minimize your attack surface
Every endpoint, feature, or open port is a potential vulnerability. Reducing unnecessary functionality reduces risk.
2. Validate and sanitize all inputs
SQL injection and cross-site scripting (XSS) are still among the most common attacks because many teams still assume “trusted” inputs exist. In reality, trust nothing.
3. Prefer secure defaults
Features that expand access or reduce protection should be opt-in, not opt-out. Developers should default to the safest configuration.
4. Encrypt everything
Data should be encrypted in transit and at rest by default. Sensitive data should also be encrypted in memory wherever possible.
5. Avoid hardcoded secrets
This includes API keys, database passwords, tokens, and certificates. Use secure vaults and rotate secrets regularly.
6. Handle errors gracefully
Verbose error messages often leak internal information. Error handling should avoid revealing implementation details.
7. Use secure dependency management
Stay current on patches, pin dependency versions, and use automated scanners.
8. Plan for failure
Assume things will break, design fail-safe mechanisms rather than fail-open behaviors.
Threat Modeling as a Development Habit
Threat modeling is one of the highest-impact secure-by-design practices. By thinking like an attacker, developers can:
- Identify weak points early
- Prioritize high-impact risks
- Understand potential attack paths
- Architect more resilient systems
Threat modeling should happen:
- At the design stage
- Whenever a major feature is added
- When external APIs or new third-party integrations are introduced
This proactive approach produces more secure systems at a fraction of the cost of fixing issues later. By incorporating threat modeling into the development lifecycle, developers can create more secure and resilient software that better protects user data and privacy. Ultimately, threat modeling is a high-impact secure-by-design practice that can greatly enhance the overall security posture of software applications.
Security-First Development in a Real-World Workflow
To bring everything together, here’s what a fully Security-First workflow might look like for a modern development team:
Planning & Design
-
Conduct threat modeling
-
Determine least-privilege access requirements
-
Document expected data flows
-
Validate vendor components or APIs
Coding
-
Use secure coding frameworks and linters
-
Run SAST tools as you code
-
Follow secure-by-design patterns
Build & Test
-
Scan dependencies (SCA tools)
-
Generate/update SBOMs automatically
-
Perform automated DAST scans
-
Validate IaC templates
Pre-Deployment
-
Enforce approval workflows
-
Verify Zero Trust policies for new workloads
-
Check compliance baselines
Deployment
-
Runtime container scanning
-
API authentication verification
-
Identity and permissions validation
Operations
-
Continuous Zero Trust enforcement
-
Real-time logging and anomaly detection
-
Automatic patching or hotfix workflows
Post-Incident Learning
-
Root-cause analysis
-
Update SBOMs, threat models, and IaC baselines
-
Improve detection and alerting rules
Common Challenges When Implementing Security-First Development
Adopting this approach is worthwhile but not easy. Organizations often encounter:
Cultural resistance - Developers may fear that security slows them down, especially when they are on a deadline. DevSecOps reframes this by making security part of the workflow, not a barrier to it.
Tool sprawl - Security tools multiply quickly. Consolidation and clear strategy are essential.
Skill gaps - Security engineering requires training. Successful organizations invest in secure coding courses, hands-on labs, regular threat modeling sessions, and security champions programs.
Inconsistent enforcement - Automated guardrails, not manual processes, ensure consistency.
Legacy systems - Older systems may not support modern standards. In these cases, compensating controls — monitoring, segmentation, and access restrictions — can provide interim protection.
The ROI of Security-First Development
Investing in security up front produces measurable returns:
Lower long-term costs - Fixing vulnerabilities early is exponentially cheaper than remedying issues after deployment.
Reduced downtime - Zero Trust and DevSecOps practices minimize blast radius and accelerate containment.
Greater customer trust - Users increasingly demand transparency, security guarantees, and proof of responsible software practices.
Supply chain resilience - SBOMs and secure dependencies protect against widespread attacks that ripple through ecosystems.
Faster recovery from incidents - With automated logging, identity controls, and dependency traceability, response teams can pinpoint and remediate problems quickly.
Long-term competitive advantage - Organizations that ship safer, more trustworthy software win market confidence — especially in regulated industries.
How to Begin the Transition to Security-First Development
Whether your team is building from scratch or modernizing existing processes, you can begin transforming toward a Security-First approach in manageable steps.
1. Start with visibility
Begin by scanning your existing codebases, infrastructure, and cloud configurations. You can’t secure what you can’t see.
2. Build (or retrain) a cross-functional security squad
Security champions embedded within each team dramatically improve adoption and culture.
3. Automate the simplest pieces first
Dependency scanning, static analysis, and secrets detection are easy to automate and produce immediate value.
4. Introduce SBOM generation into your pipelines
Even if you're not yet required to produce them, SBOMs give you visibility and accelerate vulnerability management.
5. Define your Zero Trust roadmap
Start with identity hardening (MFA, conditional access), then segment networks, then apply workload identities and micro-segmentation.
6. Integrate threat modeling sessions into your development lifecycle
Make it a standard step in feature planning or sprint kickoff.
7. Document and socialize secure-by-design standards
Developers need clear examples, patterns, and reusable templates.
8. Measure your progress
Track metrics like:
-
Mean Time to Remediate vulnerabilities
-
Number of vulnerabilities discovered pre- vs post-production
-
Coverage of automated scans
-
Dependency freshness
-
Privilege creep trends
The Future of Security-First Development
Security-first isn’t a trend — it’s becoming a foundational requirement for all modern software.
Expect to see increased adoption of:
-
AI-assisted secure coding
-
Automatic SBOM validation during procurement
-
Infrastructure attestation and verifiable builds
-
“Compliance as code” frameworks
-
Ephemeral infrastructure with built-in policy enforcement
-
Standardized Zero Trust maturity models
Organizations that embrace these models early will be better prepared for regulatory changes, threat evolution, and customer expectations.
Final Thoughts
Security-First Development is more than a set of practices — it’s a mindset shift. It asks teams to treat security with the same level of importance as performance, scalability, or usability.
By embracing DevSecOps, generating and maintaining SBOMs, adopting Zero Trust architectures, and following secure-by-design principles, organizations can build software that’s not just functional and fast — but resilient, trustworthy, and prepared for the realities of today’s threat landscape.
How CSW Solutions Helps You Build Security-First Software
Security-first development isn’t just a best practice, it’s a competitive advantage. But adopting DevSecOps, generating accurate SBOMs, implementing Zero Trust principles, and shifting to secure-by-design engineering can feel overwhelming without the right partner. That’s where CSW Solutions comes in.
At CSW Solutions, we help organizations modernize their software development lifecycle with a security foundation baked in from day one. Our team combines deep cloud expertise, Microsoft-focused engineering, and hands-on security guidance to help you:
-
Integrate DevSecOps into your pipelines
We streamline your CI/CD processes with automated scanning, secure configuration baselines, and continuous validation without slowing down delivery. -
Generate, manage, and operationalize SBOMs
We help you build SBOM generation into your build workflows, interpret results, and use them for real supply-chain resilience. -
Adopt Zero Trust architecture across your applications and cloud environment
From identity hardening to micro-segmentation and secure API communication, we help you design systems that assume breach and minimize impact. -
Shift your teams toward secure-by-design engineering
Through threat modeling workshops, secure coding patterns, and reusable templates, we empower your developers to make safer decisions every day.
Whether you're modernizing legacy applications, building new cloud-native systems, or strengthening your compliance posture, CSW Solutions delivers the guidance, tooling, and engineering support needed to move from reactive security to a truly Security-First Development culture. We support our work even after it's all said and done, so if there are ever any issues, we are here for you.
If you're ready to strengthen your software from the inside out, our team is here to help you get started.
